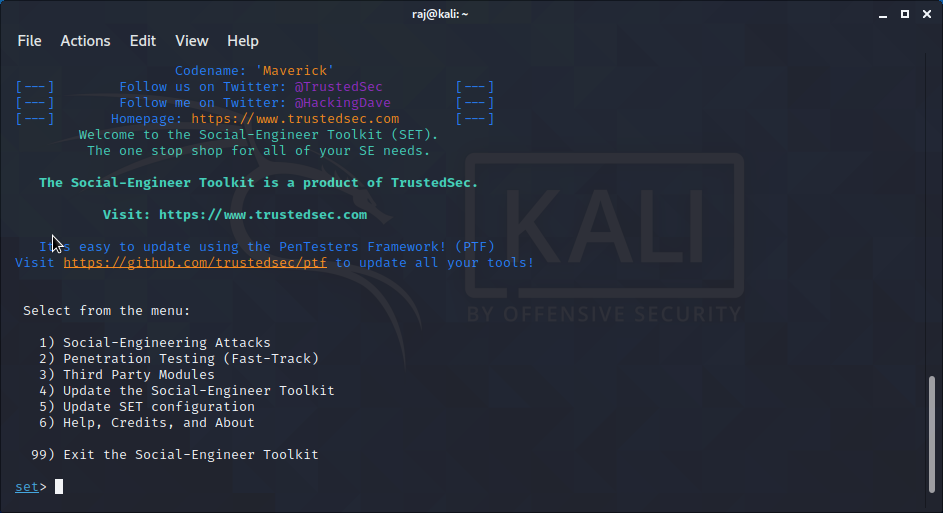
What is Spear phishing?
Requirements
Termux or Linux How to install setoolkit in termux
Spear phishing attack
Once you choose social engineering attack vector you can see 10 module see this above picture now choose first option 1. Spear-Phishing Attack Vector
The Spearphishing module allows you to specially craft email messages and send them to a large (or small) number of people with attached fileformat malicious payloads. If you want to spoof your email address, be sure “Sendmail” is installed
sudo sendmailconfig
Once you install sendmail config then start it so type this below command in your terminal
sudo service apache2 restart
Once you complete above all thinks you choose first option 1. Perform a Mass Email Attack
Now you can see lot’s of payloads you can choose which payload you want but I choose 1st payload. Once you choose payload It will ask IP address so type your local IP address or Ngrok IP address.
Once you type ip address it will ask which injection type you will choose so select which you want i choose 1st option.
Now type port number and Select the payload you want to deliver via shellcode injection
The DLL Hijacker vulnerability will allow normal file extenstions to call local (or remote) .dll files that can then call your payload or executable. In this scenario it will compact the attack in a zip file
and when the user opens the file extension, will trigger the dll then ultimately our payload. During the time of this release, all of these file extensions were tested and appear to work and are not patched. This
will continiously be updated as time goes on.
Now you set output file name and choose file format see this below image.
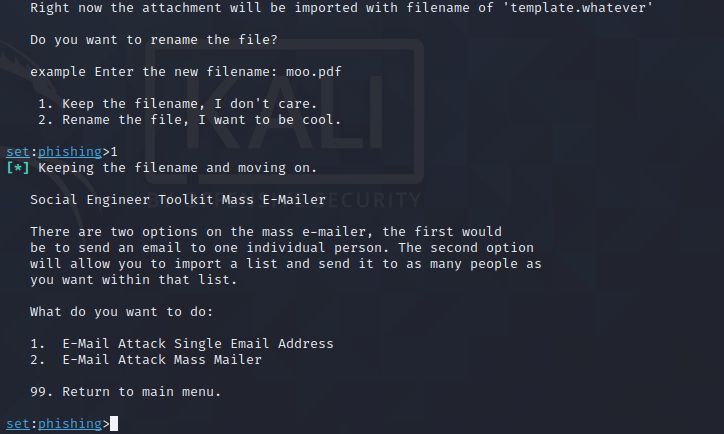
Now you choose email attack type mass or single
Once you choose email attack type now you choose email template
Once you type your victim email address this tool give two option to you if you have own server means choose 2nd option that’s better or else choose 1st option use any fake email account but the email account have this following condition.
- Email account should not enable two way factor authentication
- Email account must be enabled less-secure-app
If you have above 2 condition this attack will work otherwise this hack not work.
Once you complete this above all process your payload was sent to your victim once your victim click your payload. You can access your victim device remotely.















إرسال تعليق