What isJava applet vector?
The Java Applet Attack method will spoof a Java Certificate and deliver a metasploit based payload. Uses a customized java applet created by Thomas Werth to deliver the payload.
Requirement’s
- Termux or Linux : How to install setoolkit in termux
How to use java applet attack vector
Step 1: Open Setoolkit
sudo setoolkit
Step 2: choose attacking vector
Step 3: choosing attacking method
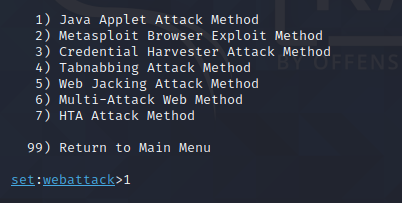
Now we choose java applet attack method so type No 1 and press enter
Step 4: Choose web attack
Once you choose java applet attack method you can see this below three option
This is first method will allow SET to import a list of pre-defined web applications that it can utilize within the attack.
2. Site Cloner
This is second method will completely clone a website of your choosing and allow you to utilize the attack vectors within the completely same web application you were attempting to clone.
3. Custom Import
The third method allows you to import your own website, note that you should only have an index.html when using the import website functionality.
You choose any one which you want I choose 2nd option
Step 5: Choose Certificate
Once you complete above all process now choose certificate which you want I choose second option
Step 6: Choose Website and payload
Now choose phishing website and payload option I choose phishing website: www.facebook.com but you choose any website and I choose payload for meterpreter memory injection.
Once you choose website and payload set port number and shell code injection see this below image.
Step 7: Share link to victim
Now you will get one metasploit shareable link share that link to victim see this below image
Once you victim click this link your payload automatically executed and you will get session. see this below image.








إرسال تعليق